Firefox has (unfortunately) lagged behind other browsers recently when it comes to implementing the more secure TLS 1.2 and it’s only now officially landing in the upcoming release 27. It can always use more testing though and if you’re running version 26 you can still enable it and test.
Browse to:
about:config
Set the following:
security.tls.version.max:3
This is the maximum supported protocol so it doesn’t mean that the sites you visit will now be using TLS 1.2. If you want to (try and) force it, there is a security.tls.version.min but be warned that probably most of your sites will fail.
You may also wish to disable this deprecated SSL3 algorithm:
security.ssl3.rsa_fips_des_ede3_sha:false
You can test this out by browsing to http://howsmyssl.com.
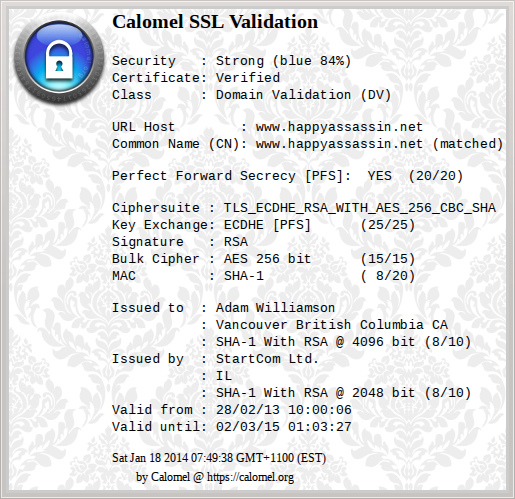
Calomel is a handy addon (BSD licence) to tell you what your secure connection negotiated to when you visit a site and gives it a score.
If you notice breakage, please report upstream.

4 thoughts on “Enable and test TLS 1.2 in Firefox 26”
Thanks for the tips! Helpful, and reminded me to update my server’s cipher suite since I can do TLS v1.2 now (yay).
However, I’m not sure about Calomel: the domain seems to have expired, and it seems to consider TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA “0/39 very weak”, which I don’t think is right.
Hey Adam, yeah that doesn’t seem right. When I visit happyassassin I get 84% (one of the highest I’ve seen) and it seems perfectly happy with ECDHE AES 256 SHA, you just lost a few points for SHA-1 as far as I can tell. Where did you see the 0/39?
Just about every single site I visit, after I tweaked the Firefox config as per your blog post. Maybe I got an old version of the extension or something?
I’m running version 0.66 of Calomel. Do you get that even when you go to happyassassin? I get this: